- meoward
- Posts
- 🐈 200k routers seeking good homes
🐈 200k routers seeking good homes
Plus burnout. Is PTO the solution?

Read time: 5 minutesChuckles: 16
Hi again, it's meoward – your inbox's weekly dose of security. Reading this email will make you smarter and more likeable. Guaranteed, or your money back.
On the stack this week:
🪲 200k exploitable routers on the Internet: SOHO routers can't catch a break. This time it's DrayTek with an unauthenticated remote code execution vulnerability.
💳 Reputable looking phishing links: brought to you by SnapChat and American Express. How does the slogan go... don't leave home without an open redirect?
🙏🏻 Silicon Apologies: Twitter leaked emails and phone numbers. Twilio was breached. And Slack shared your hashed password.
🕯Burnout is real: I took a 2 week vacation. Did it help?
Chop, chop. Look lively now.
We need blue team people to start writing malware that can move laterally and persist and all that good shit but the payload is to enable PowerShell logging and install Sysmon 😂
— Nasreddine Bencherchali (@nas_bench)
4:05 PM • Jul 28, 2022
All your DrayTek routers are mine
SOHO routers suck. (That's small office / home office, not the London neighborhood). They run outdated Linux kernels. Vendors often fail to patch core components like VPN and multimedia software. And last year we saw high scoring CVE's for the likes of Netgear, Asus, Synology, D-Link, and many others.
You can add DrayTek and 29 of their routers to that list. Skrillex Trellix researchers found a highly exploitable remote code execution vulnerability in DrayTek's router management interface. The impact is full control granting an attacker the ability to pivot into the victim's internal network.
And while this already sounds bad, it gets even worse when you see how many of these devices are on the Internet.
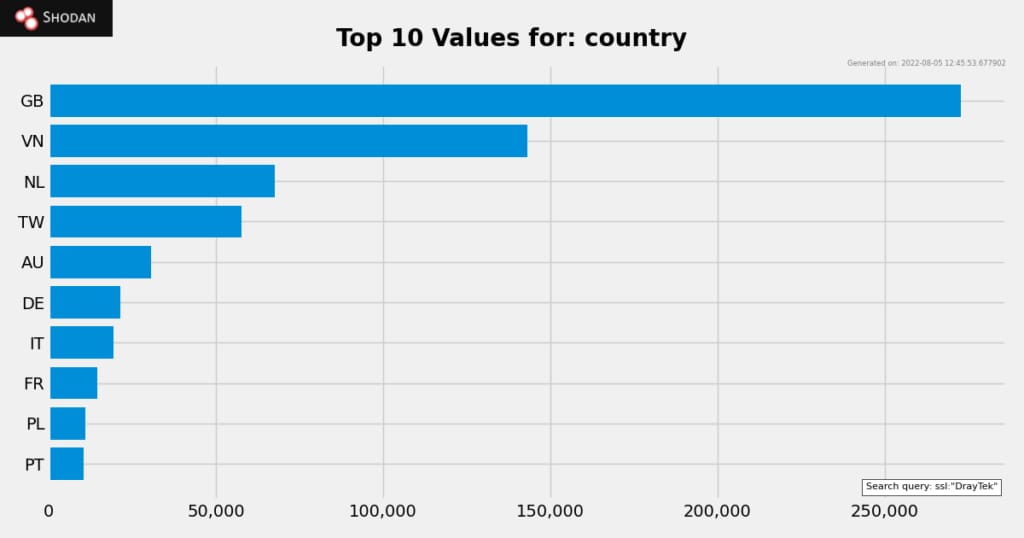
Maybe they're all in Soho, London?
SnapChat and Amex websites used for phishing campaigns
Open redirects are one of the most underrated vulnerabilities out there. Why? Phishing. Remember what you learned in your annual phishing training? Don't click links to websites you don't trust!
But what if an attacker could send you a phishing link using snapchat[.]com or americanexpress[.]com?
Normal URL redirects happen when a website wants to send you from one location to another (the target). But sometimes web developers allow user input to define the target location. This can lead to what's called an open redirect vulnerability. An attacker can use these vulnerabilities to redirect users to malicious websites.
Researchers at INKY detected phishing campaigns using both the SnapChat and Amex domains. The threat actors were exploiting open redirects to create reputable looking phishing links.
Amex fixed the issue within a couple days. SnapChat received a bug bounty report for the vulnerability last year. It's still not fixed.
Maybe I'll start using SnapChat's open redirect as my primary subscribe link.

Twitter, Twilio, & Slack. Oh my!
I got a lot of apology letters this week. Here's the quick version:

Last week, the profiles of 5.4 million Twitter users was posted for sale on a hacker forum. These profiles included verified emails and phone numbers. The original price was $30k, and it was purchase by two different threat actors for a negotiated price.
Twitter learned about the vulnerability back in December thanks to a HackerOne bug bounty. They patched the vulnerability in January.
The threat actors that purchased the profiles will likely release the data for free in the future.
Twilio

Several Twilio employees received SMS phishing messages with links to cloned Twilio sign-in pages. A few employees entered their username and password. This allowed an unnamed threat actor to gain access to Twilio customer account data. They're sorry.
Slack
I'm super lazy. Instead of inviting people one-by-one to my Slack workspace, I create one of those shared links. Then I can send it to anyone I want to join. Seemed fine.
But from April 17, 2017 to July 17, 2022, if you created one of those links, Slack also sent your hashed password to anybody online in that workspace.
Slack uses websockets to stream data, including behind-the-scenes information. One of these hidden events: shared invite link creation or revocation. But this event also included the hashed password of the user creating or revoking the link. Womp womp.

Me staring at the developer who decided to jsonify the entire object and sent it.
It sounds bad (and it is), but nobody probably saw it. Unless someone was inspecting the websocket data from Slack when I created the link. 🤞🏻
Does taking a vacation help prevent burnout?

I've been a bit burned out recently. So, I took a 2 week vacation. No emails. No slack. Not even a text message. Total disconnect from work.
Did I come back energized and renewed? Yes. But the better question to ask is: how long will it last?
A bunch of smart people researched the impact vacation has on burnout and found that vacations don't prevent burnout. And the reason is obvious, but I'm putting it right here in the text so you get it:
Whatever is causing you stress at work will still be there when you return. When you take a vacation, you're only temporarily getting away from the issue. If those chronic stressors aren't addressed, your burnout resumes.
And burnout comes back fast. Studies have shown that the benefits of a vacation can be gone in that first week back to work.
In short, if you're burned out at work, take a vacation. Enjoy it. Do something fun. But when you get back, identify the root cause of your chronic stressors and do something about it.
And then go take another vacation!
Snacks
⊹ [matrix] Microsoft decided to recreate the MITRE ATT&CK matrix with their own version for Azure (there is actually a good reason btw).
👀 [tool] Hunting for duplicate SSH keys just got a lot easier.
🚦 [standard] After 5 years of waiting, the Traffic Light Protocol v2.0 is released. WHITE is now CLEAR.
🐟 [template] Google Meet phishing template For Gophish.
🧭 [blog] Microsoft Office, now with debugging symbols.

How did you like today's email? |

